What is Locky Ransomware?
Table of Contents
- By Greg Brown
- Published: Jan 20, 2023
- Last Updated: Jan 25, 2023
Ransomware is one of the most devastating cyber threats of the modern age. Predators use ransomware as an extreme attack vector with the same goal as centuries-old blackmailing outlaws; extort money.
Ransomware attacks are as old as the internet; the first documented attack happened in 1989 via floppy disks. AIDS Trojan or PC Cyborg Trojan encrypted all the directory names on the C Drive. A Harvard evolutionary biologist developed the malware.
Ransomware has evolved into some of the most dangerous, costly, and debilitating assault vectors in history. Targets include online banking and financial services to government and conglomerate infrastructure. Staggering losses in the billions of dollars have made attacks such as WannaCry and REvil malware household names in cyber security.
Saudi Aramco, the world’s largest gas and oil producer, faced a devastating cyber extortion attack in 2012. The suspected, first known state-sponsored attack cost the oil producer millions of dollars. In a matter of hours, 35 thousand company computers were partially wiped of data, with five thousand machines rendered totally useless. The attack sent Saudi Aramco’s computer network back to the stone age. A single employee opened a phishing email that downloaded the malware and started the assault.
Locky Ransomware
The high-profile Locky malware was first noticed in 2016 and was actively used by the Dridex Gang. By late 2017, Dridex was the 800 lb. gorilla in banking and financial malware. The group quickly realized the tremendous potential of ransomware and is now responsible for significant attacks worldwide.
The original Locky Ransomware code has disappeared. However, variants of the Locky ransomware family have grown in popularity.
Locky is a phishing attack, delivered as an attachment by the MS Office downloader or JavaScript. The core of the Locky malware is a Windows executable file. Once the malware has been deployed, it disappears and runs from a copy attached to the temp folder.
Once the Locky malware begins its assault, each file is encrypted and renamed. The first characters usually contain the name of the victim and then other random numbers and letters. The extension is changed to .locky, typical of a ransomware attack.
Cyber experts continue to analyze encrypted Locky files and find there is complete entropy to the assaults. With no visible patterns, Locky Ransomware is one of the most malicious malware codes to be released to the public.
Locky adds a few specific entries into the Windows registry, the most significant being the Autorun key. The Windows autorun key gives instructions to the malware to start automatically after reboot.
Wallpaper
Locky malware attacks the three types of hard drives: fixed (usually the C drive or any named configuration), removable drives, and ramdisk. After execution, Locky moves laterally through each drive and begins to map and attack any connected networks.
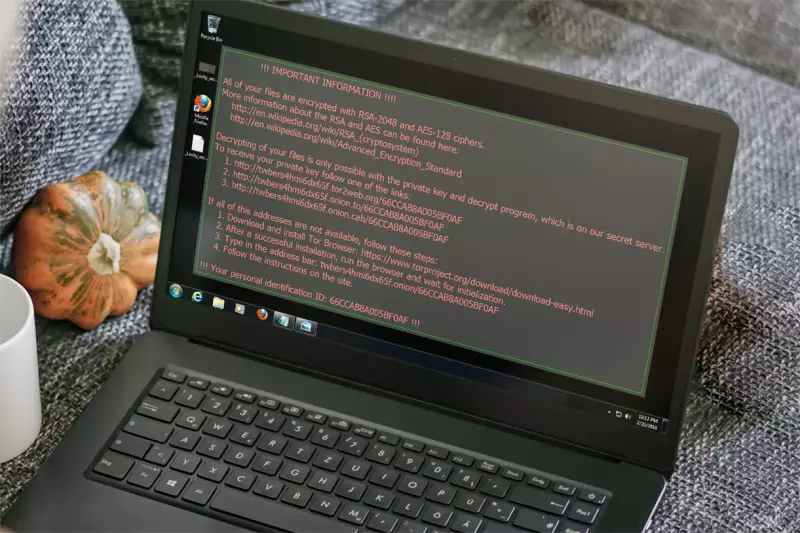
Infected machines display a ransom note immediately after the execution of the virus. Wallpaper instructions to the owner (prepared in several languages) show how the victim can pay and release their machine. Each Locky wallpaper gives its owner the helplessness of their situation and instructs them to visit a predetermined website.
Instructions demand owners to install the TOR browser. The wallpaper contains a unique ID for each infected machine or network. Once the ransom has been paid, a decryption key is given to the owner. Victims must type in the attack ID and a bitcoin code into a form, after which a decryptor program is sent by email.
Defend Against Locky

Since its inception, Locky has gained notoriety due to the global gang Dridex using that specific malware in most of their attacks. Additional reasons for Locky’s popularity are its comprehensive spread attack features. Once deployed to a user’s machine, Locky can map out and infect a global network within hours.
After comprehensive inspections of the virus, most cyber experts agree that Locky is a vicious malware code with similar features to other ransomware codes. This commonality means individual users and network admins can use aggressive mitigation techniques already on the board.
Microsoft and its legal team traced the servers of the Locky Ransomware and threatened them with legal action. The company also laid down several actions that network admins and individual users can take to mitigate the virus.
- Phishing and spam are the most prevalent ways attackers infect networks with ransomware. Make certain email gateways are protected. It is essential to use endpoint security for detecting and blocking malicious emails. A robust endpoint security solution protects against attachments and infected URLs in emails. Regularly patch network systems and conduct vulnerability assessments.
- Make it easier for employees and customers to do the right thing in protecting company assets. In the absence of training, employees make poor decisions with their technology. Create common sense policies for every person who has access to company technology. Make sure systems and controls are taught regularly so everyone can do their job effectively. It is advisable to make sure policies are not cumbersome or restrictive.
- Attackers do not seek out impenetrable firewalls to access company networks. Predators always look for weak points, such as over-trusting or unwitting employees. More employees are working from home with little training made available, and attackers have increased their use of phishing to infect a company’s network.
- Implement anti-phishing campaigns to block malicious downloads and websites. Secure web gateways can scan a customer’s web traffic to identify malware ads, leading to a ransomware attack. Identifying threats before they become a significant problem is the key to successfully mitigating ransomware. Most web breaches result from simple failures and a breakdown in planning rather than attacker ingenuity.
- Implement a Zero Trust security model as soon as possible. Zero Trust is a security framework requiring all users to identify and authenticate themselves before authorization, regardless of whether they are in or outside the network. Users are continually authenticated when on the network to have the ability to access company applications.
Segmenting the network is the first and one of the most important aspects of a zero-trust security model. Network segmentation breaks the entire network down into smaller manageable parts.
















