What is Data Encryption, and How Does It Protect You?
Table of Contents
- By Dawna M. Roberts
- Published: Apr 01, 2022
- Last Updated: Mar 27, 2023

Data encryption is a term widely used in the cybersecurity community. However, most people who use encryption on a day-to-day basis don’t really understand what it means. Data encryption is essential to digital privacy and security.
What is Data Encryption?
Encryption is a process of scrambling information and making it unreadable. The purpose of encryption is to protect data when you send it, store it, or receive it. The types of data protected by encryption can be almost anything, including email, text messages, files, bank details, usernames and passwords, and even medical and fitness logs.
How Does Encryption Work?
With so much of our personal and private information stored online and in cloud services, encryption is necessary to keep information away from hackers.
Encryption works by converting plain text such as an email or text message into an unreadable format called “ciphertext.” Once the data reaches its destination, it is once again converted back to plain text. To make it work, both the sending and receiving devices need to have a secret encryption key to lock and unlock the information. It is accomplished through complex algorithms.

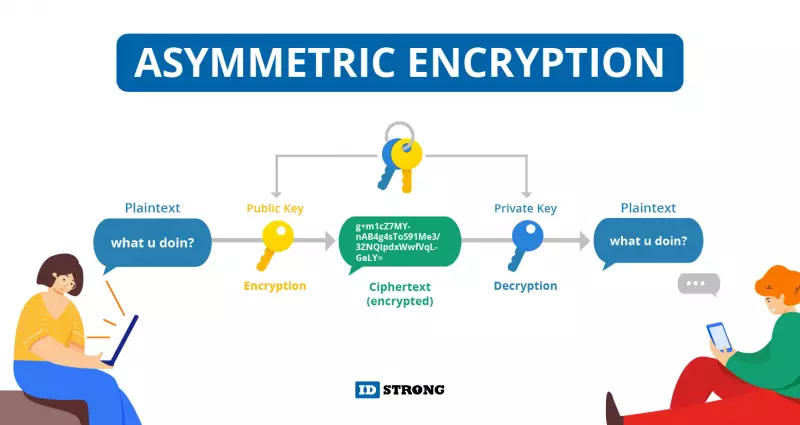
There are two types of encryption keys symmetric and asymmetric. Symmetric encryption uses one password to create a unique secret key. Asymmetric encryption uses two keys to lock and unlock data. One of these is called a public key, and the other is called a private key. The public key may be shared among many users, but the private key is only held by one person.
Types of Encryption
Within the vast world of encryption, there are many different types. Each was designed with a specific security need in mind. The most common types include:
Data Encryption Standard (DES)
DES is very low-level encryption, and it dates back to 1977. This format is barely ever used in the real world because more advanced algorithms are much more effective.
Triple DES
Because DES is a relatively weak type of encryption, triple DES runs it three times for better protection. Essentially, it encrypts, decrypts, and then encrypts the data once again. However, even triple DES is not recommended for protecting sensitive information.
RSA
RSA, however, is a very strong encryption method used by many software and hardware vendors. The letters stand for three computer scientists, and it uses an advanced algorithm combined with a long key length making it excellent for protection.
Advanced Encryption Standard (AES)
As of 2002, the U.S. government adopted AES as the standard encryption for ultimate protection.
TwoFish
TwoFish is another type of encryption used by hardware and software manufacturers. It is considered one the fastest on the market.
SSL
Most websites use a secure socket layer (SSL) for encryption when transmitting data or saving form submissions. Whenever you visit a website and see the little lock next to the URL, that means the site is protected using an SSL. The URL will also show as HTTPS and not HTTP. Never enter data on a website or make a purchase if you do not see the lock symbol or HTTPS in the web address.
Why Use Data Encryption?
Even understanding how encryption works, you may still wonder why use it? There are some excellent reasons to turn on encryption within all your digital systems. These reasons include:
Privacy - Digital privacy is more important now than ever before. With data breaches in the news, ransomware around every corner, and hackers at the door, you cannot be too careful when protecting your own information and keeping it away from identity thieves. Most mobile devices include built-in options for encryption. Be sure to only use encrypted email when sending personal or sensitive information.
Hacking/Data Breaches - Data encryption can help companies in the event of a data breach. Even if a hacker exfiltrates the data, they may never be able to view or use it, if it is encrypted.
Laws/Regulations - As cybercrime becomes a larger issue, governments continuously update privacy laws and demand specific cybersecurity requirements, especially with companies that store data. One example is the healthcare industry and the Health Insurance Portability and Accountability Act (HIPAA). Additionally, the Family Education Rights and Privacy Act (FERPA) and the Fair Credit Practices Act (FCPA) demand that anyone collecting and storing data must comply with strict cybersecurity mandates, and often that includes data encryption.
Encryption is offered with most electronic devices and software programs. Be sure to protect all your data by turning on data encryption so that attackers cannot access your details, even if they hack into your system.
Can Encryption Be Used Against You?
Yes. Hackers use ransomware to encrypt data from hard drives and entire networked systems. They lock every file and program and make it impossible for the owner/user to access their data. Then they demand a ransom to unlock it. However, typically, the decryption keys the hackers offer do not actually unlock the data.

Ransomware and data encryption can be crippling to an organization without solid backups and a disaster recovery plan.
Tips on How to Protect Yourself
Although nothing can guarantee your digital safety, you can take steps to protect your data using encryption and other safety measures.
- Turn on data encryption on your mobile devices and all computers.
- Lock all devices with biometrics or at least long passwords/passcodes.
- Turn on two-factor authentication or multi-factor authentication when available.
- Always use long, strong passwords made up of letters (upper and lower case), numbers, and symbols.
- Install good antivirus/anti-malware software on all devices.
- Keep all your software updated and hardware patched with the latest security updates.
- Keep good backups of all your data.
- Never click links in email or text messages. Investigate where they came from first.
- Never download attachments from email or software from untrusted sources.
- Store your data in a trusted cloud environment.
- Never pay the ransom. Restore your systems and data from solid backups instead.
















