What is the NIST Cybersecurity Framework
Table of Contents
- By Greg Brown
- Published: Jul 17, 2023
- Last Updated: Jul 28, 2023

Created in 1901, the National Institute of Standards and Technology (NIST) was established to remove several challenges to US Industrial competitiveness. At the time of the NIST creation, the United States was considered a second-rate measurement infrastructure, lagging behind the United Kingdom, Germany, and other countries.
The NIST has evolved into a comprehensive framework of guidelines and best practices for businesses to manage their security in a cyber-attack world. Similar to other powerful cyber frameworks, the NIST is a federal agency within the US Department of Commerce.
What is the NIST Cybersecurity Framework?
The Framework is designed to foster cybersecurity risk management and communications from internal and external organizational stakeholders. The structure is based on existing guidelines and standards to mitigate risk and is designed for companies and organizations that are part of the US Infrastructure.
NIST Framework is voluntary and is not a regulatory agency of the US Government. However, in May of 2017, Executive Order 138000 required federal agencies and some state organizations to adopt the Framework. A few organizations may require their customers to implement the NIST Framework.
Organizations use the current Framework in a variety of ways. 1) Some use the structure to raise awareness for communicating within their organization, which may include executive-level leadership. 2) Organizations map the Framework to current cybersecurity management approaches. 3) Companies and agencies are learning how they match up with each separate guideline. 4) A few agencies use the Framework to reconcile internal policy with current regulations and industry best practices. 5) The Framework is also used as a strategic planning tool to assess risk and current practice.
What are the Elements of the NIST Framework?
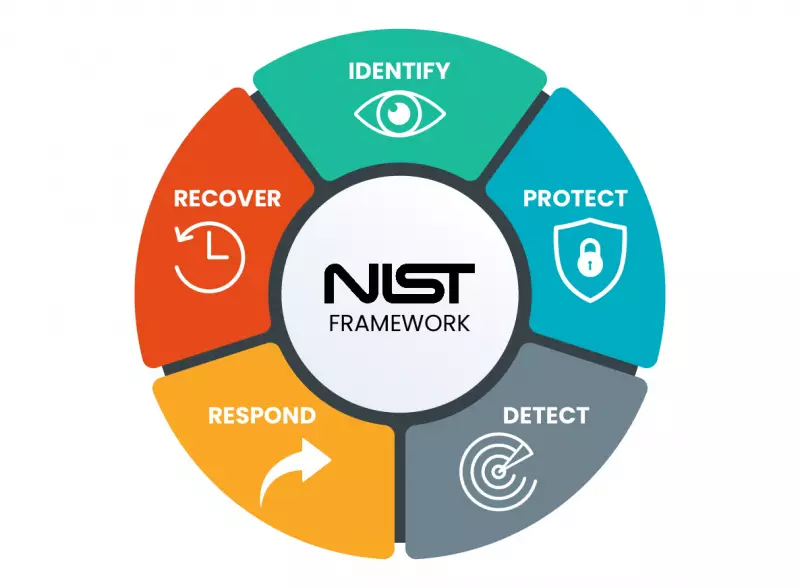
Five functions of the Core are the backbone of the NIST Framework. All other elements in the NIST structure are organized around these five elements. Each function was selected because they represent the five foundations for a successful and holistic cybersecurity program. Core elements aid organizations in cyber security risk management.
- Identity helps organizations better understand and manage cybersecurity risk to their systems, people, assets, data, and capabilities. Understanding cybersecurity risks enables organizations to prioritize and focus its efforts in a consistent manner equal to the risk management strategy and needs.
Categories Within This Function:
- Identify physical and software assets
- Identify the business environment and the organization’s role in the supply chain
- Define and identify cybersecurity policies
- Supply Chain risk management
- The Protect function outlines appropriate safeguards ensuring critical infrastructure delivery. It supports or limits an organization’s ability to contain potential cybersecurity threats.
Categories:
- Identity management and access control protections
- Empowering staff through awareness and training. Role-based and user-privileged training.
- Establish data protection security policies
- Information protection processes implementation
- Managing protective technology
- Detect appropriate activities identifying the occurrence of a cybersecurity event and enables timely discovery.
Categories:
- Ensuring anomalies and cyber events are detected and the potential impact is understood.
- Continuous security monitoring is implemented to monitor cybersecurity events. Verify the effectiveness of protective measures.
- Maintain protection policies to provide staff awareness.
- Respond with appropriate activities and take action regarding a cybersecurity incident. Respond and support the organization’s ability to impact a potential threat.
Categories:
- Ensure response planning processes are executed during and after a cyber-attack. Managing communications with law enforcement and external stakeholders.
- Conducting proper analysis to ensure adequate support and response includes forensic analysis and impact.
- Mitigation activities are performed to ensure no further expansion of the threat.
- The organization begins to analyze and incorporate lessons learned.
- Recover identifies activities to maintain plans for resiliency and restoration of services and capabilities impacted by the event. Supports timely recovery to normal operations and reduces impact.
Categories:
- Implement recovery planning processes to restore systems and assets.
- Implement improvements based on lessons learned and review existing strategies.
- Internal and external communications are coordinated following recovery.
What are the Objectives of Framework?
Since the turn of the century, governments have been combating global cyber security attacks from every angle. The NIST Framework is described as a living, breathing entity, constantly evolving and updating to meet the current cyber challenges of the day. Version 1.1 is the current iteration of the Framework, and its Core, and Version 2.0 is on the way.
NIST’s website is a comprehensive compilation of FAQs, versions, and varying degrees of resources to make it possible for businesses of all sizes to have the tools necessary to fight cybercrime. The Framework attempts to start a cyber crime initiative or add to an existing section.
One of the most valuable documents is NISTIR 8286, a resource to help the enterprise combat cybercrime. The entry page offers several schemas and other resources to help. A comprehensive computer resource center is available to anyone wanting to guard their business against the latest attack vectors. White papers, journal articles, conference papers, books, and much more are available for download.
Why The NIST Framework Matters?
Cyber attacks and threats continue to skyrocket around the globe with no apparent letup. However, private enterprises, governments, and many more are finally banding together to bring the best the world offers to confront and defeat the scourge.
Ransomware, malware code, phishing, and smishing are never-ending. The single biggest threat to an enterprise is the unwitting nature of its employees. No matter how many times they are told, and the amount of training never stops, email attachments and links are still clicked on with haphazard abandonment. Some of the most extensive network intrusions in history happened because a single employee wanted to take a peek at one of their attachments. Only after the unwitting employee is controlled will there be a significant drop in cybercrime.
















